On Oct 21st Internet has experienced a huge outage like never before, when it happened I was browsing Internet as usual and was totally unaware of the million cries overseas, most of the people in US suffered Internet blackout and fortunately some went outside of their caves and socialized with other human beings, except the SJWs who got PTSD over the whole matter. Good or bad? I don’t know, nor I cared because my Internet was working just fine. The point is, majority of the sites were not accessible/extremely slow in eastern part of the US for hours! That was a big deal, Libya has the worst Internet Speed in the entire galaxy besides their ongoing crisis, that didn’t stop ahmed from downloading Mia Khalifa’s pictures, does it matter? No, because nobody gives a fuck about Ahmed or his country, fortunately India is at
5th place among the world’s top 10 countries with slowest internet connection, poor ahmed is at 1st place (link), but unfortunately in this case Uncle Sam was the victim, ya, the only country in the entire planet where Aliens prefer to land and talk in English, so any problem in the US is a problem for the entire world because MURICA!
What is this rant about then? This is definitely not about US or the impending World War III, NO! It so happens that I felt bit responsible out of my lazy life after reading some lame articles with stupid headlines explaining this case of Internet outage to the already lame people, as a responsible netizen, yes I am! I thought of putting down my own words on the whole matter, after all, it’s part of my work life.
I’ll try my best not to put more technical details and confuse the shit out of you. Take a pinch of salt and buckle up.
In brief?
On Friday October 21, 2016 approximately at 11:10 am GMT (4:40 pm IST) Dyn experienced a huge spike in their inbound traffic which resembled the patterns of a DDoS attack, basically huge amount of traffic congesting their entire network. Dyn’s NOC (Network Operations Control) team claimed to address this by 1:20 pm GMT (6:40 pm IST) but a second wave of DDoS attack started at 3:50 pm GMT (9:20 pm IST) which targeted global infrastructure of Dyn, not just in US. As like in previous attack, Dyn mitigated this one too by 5 pm GMT (10:30 pm IST)
I know, you must be wondering who is Dyn and what is a DDoS? Don’t worry I’ll explain all. Dyn is a well known company (at least in computer networks world) who provides solutions for Internet traffic management, intelligence, DNS services etc. They have some of the biggest customers in their pocket like Twitter, GitHub, Reddit, Amazon, Netflix, Spotify … list goes on. When the attack happened on Oct 21st, it was targeted in particular on their DNS infrastructure which is used by Dyn’s customers, the attack almost crippled their network thereby affecting its customers. DNS is a crucial part for the Internet to work, and in this case it was the primary target. I’ll explain DNS too.
Many users who tried to access the customer sites of Dyn like Twitter were shown a timed out error in their browsers, especially the users in the east coast of US. Moving on …
What the heck is a DDoS attack?
I don’t want to give its definition, that’s something you can Google out. I’ll explain what a DDoS closely looks like in a real world. Some examples:
Imagine you are on your way to buy the last signed copy of Chetan Bhagat’s One Indian Girl and you have encountered a road block due to a protest by sangh parivar condemning that women should not wear leggings and shorts in public places. While you and I doesn’t give a shit about it (I don’t give a shit about Chetan Bhagat either), all that drama by saffron brigade delayed your commute and by the time you reach the store you see a happy customer on her 30’s with ‘Proud Feminist’ written on her t-shirt entering her credit card’s pin for the last copy of your all time favorite author’s book. Without knowing what to do you check out books on Spirituality and to fill the void you end up buying “How to align your Chakras with Banana Peels”, which of course comes with free banana peels at just 999/- only.
Take another classic example, remember the days we used to book train tickets on the IRCTC website at 8:00 am in the morning for tatkal? Ever wondered why the heck it runs very slow especially at 8:00 am? For the clueless first timers who thought they can book a 1-tier AC ticket easily because there are 2 seats available while ignoring 20 available seats in 3-tier AC all for a 4 hour journey ends up with a sleeper class ticket with 22 in weighting list, only to bribe the TC to get into an AC couch later. The site opens just fine at any other time but why not at 8:00 am? I am not sure what the current times are for tatkal booking, been a while I booked.
Though the first example is vague just like Chetan Bhagat’s books, either cases have something in common, if you figured it out you can move to the next section. If not, it’s very simple, really. In both cases we have users who are trying to avail a service, which assumed to be available at all the time but couldn’t avail it at particualr time. A service can be anything, going to a store and buying a book, or opening a website and purchasing online. In the above two cases the users were not able to avail the service because of the service’s unavailability or poor performance.
In the first case it was service unavailability due to a road block, while in the second case it was poor performance to handle so many requests from the users which in turn caused a service unavailability on the IRCTC site. DDoS, which is more complex and highly technical, is in a way almost similar but can be extremely disruptive at times. To put it in simple terms.
A Denial of Service (Dos) and Distributed Denial of Service (DDoS) causes a legitimate user request to a service to either experience a huge delay or simply make the service unavailable for extended periods of time. The reasons for the service unavailability can be either internal or external factors. In this case, we study about the External factors in particular, which is what the outage on Oct 21st was about.
Best last example I can give, using an elevator at office. In the early morning hours you can use it without any problem, in peak hours you’ll have crowd but still you can use it with some amount of delay. I am not equating the other people using it to a DDoS attack. The DDoS attack here would be someone who are not suppose to use the elevator but uses it and causes inconvenience to other users who are suppose to us it. Example, Greenpeace activists intruding your office to protest on how Air Conditioning is killing our mother Earth.
Even though by nature a DDoS is purely technical, the intentions/motivations behind it are exactly the same as a Bandh/Protest, the former is controversially known as Hacktivism which happens in Cyber World, the Internet, while the latter is simply Activism which happens in a real world, it’s just that sometimes the former goes out of control and end up making news and me writing a lengthy blog post.
So what ‘exactly’ happened on Oct 21st?
DDoS attack of course, but let’s see the technical details of it. There are two things you need to know before knowing the attack on Oct 21st. IoT and DNS.
IoT:
Internet of Things. When we think about how to access Internet we usually think about PCs (Desktops), Laptops and Mobile devices like Smartphones and Tablets. Most of us don’t even know or aware that several other devices which are connected either via cable or WiFi are capable of talking to the Internet, these devices are Smart TVs, Routers, NAS (Network-attached storage), Video Cameras used for surveillance, Smart Refrigerators, Home Security Systems etc. Unlike your Window 10 laptop which can be protected with a “solid antivirus” like McAfee which claims to protect your system from hackers stealing your good for nothing bathroom selfies, these IoT devices are unregulated and are nasty! They are susceptible to attacks because they don’t have any protective mechanisms, in almost all the cases. When was the last time you heard about Kaspersky Antivirus for your Smart TV? Hmmm, you might probably hear about shit like that in coming days, after all, after this attack IoT is a lucrative area to make money for these Antivirus companies. The risk of IoT devices was already pointed out by several security professionals but none took them seriously until now.
DNS:
Domain Name System. In the very initial days of Internet a website address was just a numerical address called an IP address, ex: 144.145.34.124. It was not a big deal to remember few dozen sites with their IP addresses but the problem was, Internet started growing exponentially. A solution was provided to overcome this problem on how to memorize hundreds of website addresses, it was called DNS. This provided a very simple solution, forget about memorizing a number, instead memorize a name, like websiteformohan.com rather than 143.189.242.199, DNS will take care of converting the name to an IP address, why this has to happen? Because the Internet works on IP based communications, not name based. When you enter a website name in your browser, like www.bvkmohan.com, the DNS service in the background converts the name to an IP address, here 74.125.68.121. For this to happen, a network of DNS systems are configured in the Internet, when you enter www.bvkmohan.com in your browser, your browser asks those DNS systems for the IP address and once it has the IP address it makes the actual connection to the website and displays the page in your browser, this is simply called as Name Resolution or DNS Resolution, and this process was disrupted on the Oct 21st attack, we’ll see.
The functionality of DNS is very complex to explain in a single paragraph. This information should be more than enough to understand the events on Oct 21st, so what happened?
In simple terms, these IoZ devices sent several junk requests, ex: asking what is the IP address of something like asdjjddv.com, the traffic may not be an actual request asking an IP address of a website, it could be plain junk traffic. Fortunately their infrastructure was/is prepared for suck attacks and how to mitigate them. Then why there was an outage?
We are not talking about the zombies like in the movie Dead Alive, we are talking about World War Z here, more than 100,000 IoT devices sent their junk traffic to Dyn infrastructure, the problem here was not the attack itself, most major companies with their internet presence have measures in place for DDoS attacks and can mitigate them to a certain extent, the attack that happened on Oct 21st was very intense that it crippled the availability of their DNS service to the actual authentic users, so when the general public entered reddit.com they got an error saying timed out.
This happened only with the users in eastern part of the US. Not everyone got affected because Dyn is not the only DNS service provider in the Internet.
How can IoT devices attack and who is behind this?
IoT devices cannot attack all by themselves. They are not as intelligent as … let’s say a Smartphone. IoT are purpose built, they are made to do a particular task, ex: a baby monitor. Unlike a multipurpose machine like a PC or a tablet, IoT devices are pretty basic, cheap and are easy to manufacture. Ex: A NAS hard disk can be run using a very old Linux OS and just 256 MB of RAM, or even less.
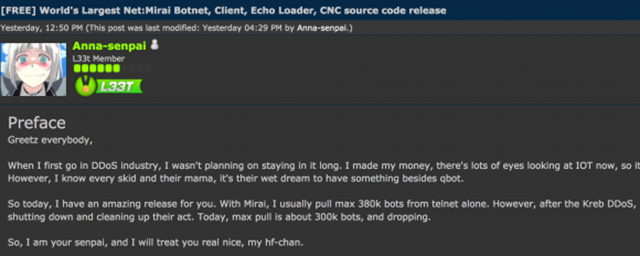
IoT devices (mostly webcams) in our case were targeted by a malware called Mirai (meaning The Future in Japanese), it was developed by a hacker who goes by the pseudonym Anna-Senpai, this wasn’t created for the attack on Dyn, this existed even before Dyn’s attack and it even helped in two other DDoS attacks. In case of Dyn, it was not exactly Mirai but a modified version of it. Just before the attack the author, Anna-Senpai, released it as an open-source in the web (link) and in just few days a modified version of Mirai was born and attacked the IoT devices to create a Botnet, which later attacked Dyn. Below is from a forum where Anna-Senpai made a post about releasing Mirai to the skids (Script Kiddies).
Botnet is a simple concept to understand and extremely complex to investigate in attacks like these. So what happened in this attack?
A malware, here Mirai, attacked a predefined group of targets (Ex: IoT devices, Desktops, Servers etc) using their default login credentials. It used a list of predefined login IDs and passwords and scanned the Internet with login attempts in a trial and error method. It used Telnet (a way to remotely login to a device) and on successful login, it made those devices part of a Botnet. Every infected device was added to the Botnet and that Botnet was controlled via CnC (Command and Control), in most cases a CnC is an infected server in the Internet which is hacked for this purpose. Below picture shows the details of the default login ids/passwords used by Mirai.
Interesting fact, from the above picture a quick lookup in Google told me that the credentials root/7ujMko0vizxv belongs to Dahua IP Cameras, looks like that company made that as a static password for all of their products, how stupid! Further googling told me that root/dreambox belongs to a product called Dreambox HD Satellite Receiver.
The hacker or a hacker group can use this CnC (via a client application or web based interface) to tell the infected devices in the Botnet to do a particular task, here in Dyn’s case they instructed the devices to send junk traffic to Dyn’s DNS servers on TCP and UDP port 53. These ports are used for DNS name resolution services. It was estimated that a traffic of 1.2 TB/s (Terabytes per second) was generated by this DDoS attack, which dwarfed every known DDoS attacked ever happened before and the result of this? The legitimate users who were using Dyn’s DNS services got affected. Big time.
The groups Anonymous and the so called New World Hackers claimed responsibility (claims to be from Russia), which is anecdotal. WikiLeaks suspected this could be a retaliation attempt by its supporters because the Ecuadorian embassy at London cut off Internet access to Julian Assange, they issued a statement regarding the same. https://twitter.com/wikileaks/status/789574436219449345
If you want to know in detail about the attack let me know in the comments, I would make another post explaing nothing but the technical details of this attack.
What was shown to people?
In the wake of this, the so called “tech authors” of many sites started writing garbage shit about the situation, as usual, only making their readers eat more shit. Some of the shitty examples below.
Technically speaking, Outage or a Blackout is the correct term to use in these cases. Shutdown is completely out of context here.
All those sites were working perfectly fine, it’s just that they were not accessible. NO! Much of the Internet was not broken!
Conclusion?
This will be a short section, I wanted to explain the actual events occurred and the details of the attack while mocking at these “Tech Sites” producing shitty articles, that’s been done. So in conclusion I want to say two things.
- It is extremely difficult to shutdown the whole Internet, no, it’s not that easy and the people who writes misinformed articles on it should be kept in a jail for their lifetime with an Internet connection of a Dial-up modem. I’ve wrote an article explaining why it is difficult, read this.
- Future is shit, this DDoS attack is just the beginning and more such attacks with even higher intensity than 1.2 TB/s are expected to happen, thanks to the IoT ready to get infected. If you’re buying a Webcam or any gadget that can be hooked to the Internet, please ensure it has some quality standards. I know you definitely don’t give a shit when going for a cheap Chinese made Webcam which has Snapchat filters but still. Regulating them is very difficult unless there are some strict standards in place, which I foolishly wish is going to happen because of this attack. The reason that I am highlighting China has no relation to the ongoing campaign in India on China products boycott, read this.
Finally, ALWAYS change the default login credentials for your networked devices/gadgets. Being said that, thanks for reading this lengthy post and share it if you think it’s informative.









No comments:
Post a Comment